Table of contents
- Virtual private clouds (VPC)
- Create vpc
- Subnets
- Create subnets
- Internet gateway
- Setting up Route tables with Internet gateway
- NAT gateways
- Setting up Route tables with NAT gateway
- Set up your RDS database
- Create the Aurora database cluster
- Create the load balancer
- Load balancer
- Create a launch Template
- Create a launch template for the Auto Scaling Groups (ASG)
- Create the ASG
- AWS WAF
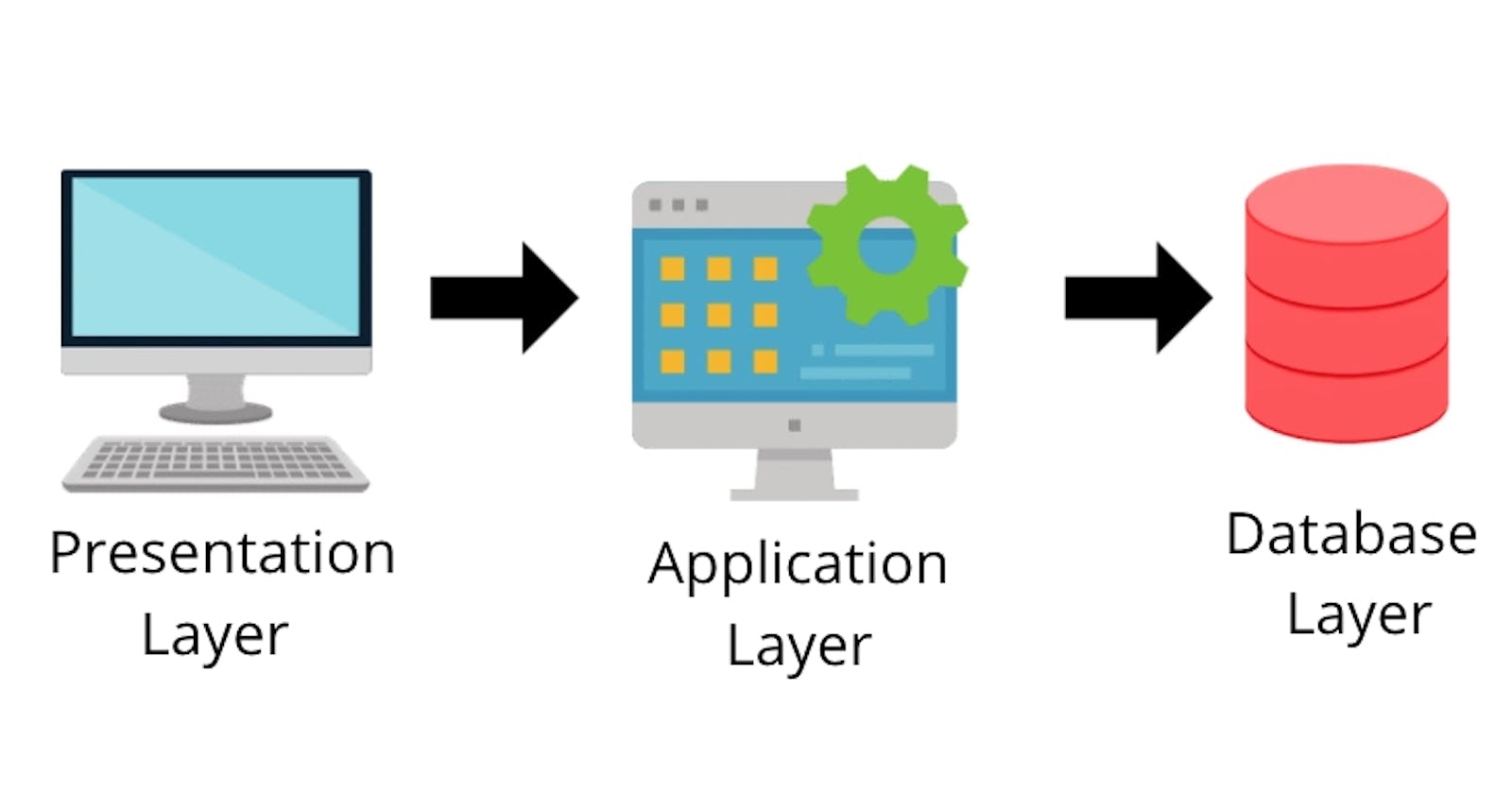
What is three-tier architecture?
Three-tier architecture is a well-established software application architecture that organizes applications into three logical and physical computing tiers: the presentation tier, or user interface; the application tier, where data is processed; and the data tier, where the data associated with the application is stored and managed.
The chief benefit of three-tier architecture is that because each tier runs on its own infrastructure, each tier can be developed simultaneously by a separate development team, and can be updated or scaled as needed without impacting the other tiers.
Virtual private clouds (VPC)
A VPC is a virtual network that closely resembles a traditional network that you'd operate in your own data center. After you create a VPC, you can add subnets.

Fig: Digramatic view of vpc
Create vpc
1.search for VPC → Create VPC →VPC Settings → Resources to create → VPC only

Subnets
A subnet is a range of IP addresses in your VPC. A subnet must reside in a single Availability Zone. After you add subnets, you can deploy AWS resources in your VPC.

Fig: Digramatic view of subnet
Create subnets
Vpc → Subnets → Create subnet


In the same way create 5 more subnets like this

Internet gateway
Our next step is to create our internet gateway and attach it to our VPC to allow public subnets traffic to the internet.
First you need to create a new Internet Gateway (IGW) from your VPC dashboard and attach it to the Three-tier-vpc VPC
Internet gateways → Create Internet gateway

I attached my VPC to the internet gateway by choosing actions, attach VPC.
Vpc(Three-tier-vpc) → Actions → Attach Three-tier-vpc
Setting up Route tables with Internet gateway
A route table contains a set of rules, called routes, that determine where network traffic from your subnet or gateway is directed.
public subnet→ Route table → Internet
privatesubnet→ Route table → Local N/w
Vpc→Route tables → Create route table

Route Tables → Actions → Edit routes and add a default route via the Internet Gateway created in the previous step .

Where as the apptier and dbtier also need routing tables , so create one table for each one of them,After creating the routing table, we have to associate the newly created routing table with the public subnets
route table → Subnet Associations →Edit subnet associations


select the two public subnets created earlier
NAT gateways
A NAT gateway is a Network Address Translation (NAT) service. You can use a NAT gateway so that instances in a private subnet can connect to services outside your VPC but external services cannot initiate a connection with those instances
Vpc→ NAT gateways→Create NAT gateway

Click Allocate Elastic IP ,then automatically the Elastic ip is allocated also create another NAT gateway for webtier-public-subnet-B.Now we have to associate subnets with the routing tables, since the webtier need the Internet we give Internet gateway and apptier,dbtier are private so we won't be exposing them to Internet so attaching NAT gateways
Setting up Route tables with NAT gateway
create route tables for each of the two Application subnets and use the NAT gateways created earlier as the default

Now, Edit the route table and add the default route via the NAT gateway in Apptier subnet A

Associate the route table with Apptier Subnet A

Similarly do the same , create a route table for Apptier Subnet B which uses the NAT gateway deployed in the another zone.
Vpc→ Resource map

The resource map shows the following
VPC


Subnets

Internet Gateway


NAT Gateway

Routes > Internet Gateway

Routes > Subnet Associations

Set up your RDS database
Create an RDS subnet group
RDS → Subnet groups → Create DB subnet group


Create the Aurora database cluster
Amazon RDS → Databases → Create database






I earlier created two sg's called Threetier-database SG and Threetier-database SG,edited the Inbound Rules of the Threetier database SG and created a rule of type MySQL / Aurora which allows traffic on port 3306 from the Threetier database Client SG.


Whatever settings I didn't mention just go with the default ones, So by default we get backup with retention period 1 day
After creating the database setup look's like this:

Create the load balancer
Create security group

Here we're selecting my IP to prevent anyone from accessing the application's web server
Load balancer
A load balancer distributes incoming application traffic across multiple targets, such as EC2 instances, in multiple Availability Zones, increasing the availability of the Threetier platform
EC2 console → Load Balancers → Create Load Balancer →Application Load Balancer




Here I clicked on create target group , To create one you need to Choose a target type select Instances, give Target group name and create target group , Now refresh in Default action in Listeners and routing


click on create load balancer
Create a launch Template
Create a security group for the Threetier servers
Edit the Inbound Rules for Threetier SG and only allow HTTP traffic on port 80 from the Threetier Load Balancer SG
Create a launch template for the Auto Scaling Groups (ASG)
In EC2 console, Instances → Create launch template




Under Additional configuration

Create the ASG
Go to EC2 dashboard, Auto Scaling → Auto Scaling Groups → Create Auto Scaling group





Keep remaining as default and create auto-scaling groups. After that, you can observe the instances created on the EC2 console. Also, grab the load balancer URL and paste it into your browser

This is how it looks
AWS WAF
AWS WAF helps you protect against common web exploits and bots that can affect availability, compromise security, or consume excessive resources.
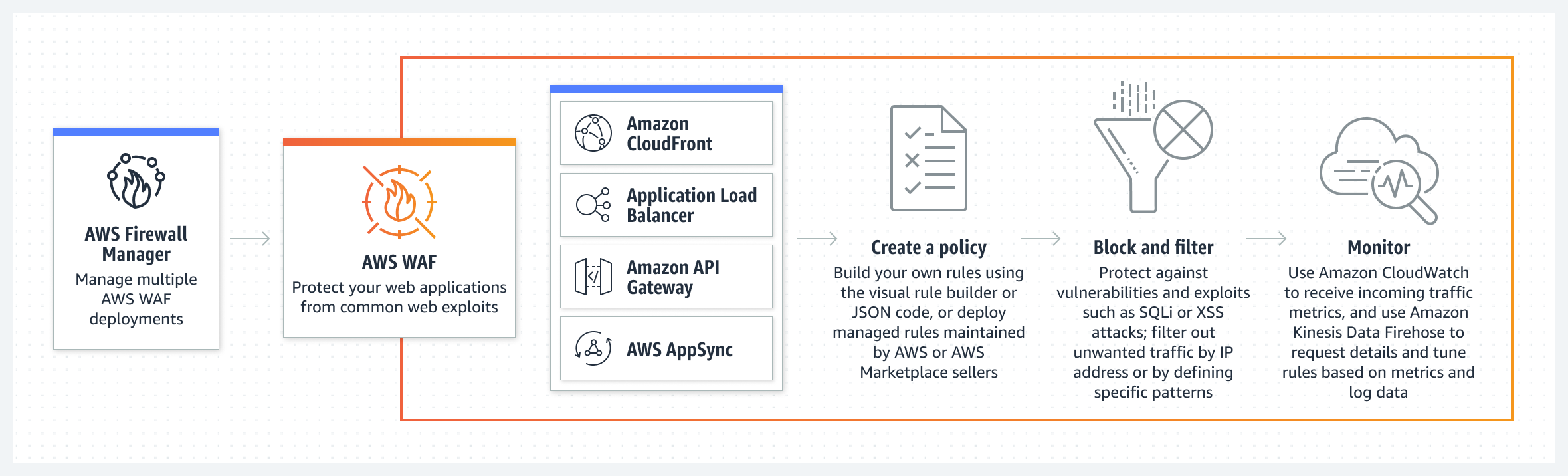
Creation of WAF
AWS WAF → IP sets → Create IP set

Here to understand the demo better i'm blocking my ip
AWS WAF → Web ACLs → Create web ACL








so, it's blocking my ip-address
AWS Backup
AWS Backup → Backup plans → Create backup plan



AWS Backup → Backup plans → Instance-backup → Assign resources


so Backup is done successfully.
Resources:
https://catalog.us-east-1.prod.workshops.aws/workshops/3de93ad5-ebbe-4258-b977-b45cdfe661f1/en-US